Key performance indicators (KPIs) allow companies to measure their progress toward goals. They give you a way of checking in to see how you’re doing. Cyber security KPI metrics provide an assessment method to give you insight into whether you’re at risk and if you’re doing enough to keep your company safe.
Cyber attacks are a very real threat. The FBI reports that its Internet Crime Complaint Center handled 800,944 incidents in 2022, amounting to $10.2B of potential losses. We could go on about the essential support cybersecurity offers, but let’s discuss what you can actually do about it instead.
What KPIs are most important for overseeing a cyber security program?
With so much data available today, it’s easy to find metrics you may be interested in tracking. Think about this from a business standpoint. Wouldn’t you like to know how cybercriminals are trying to access your business’s data?
Tracking KPIs offers outstanding benefits to your organization. KPI identification helps reduce risks, aids in early warning of unrealized risk, and provides transparency.
To select cybersecurity KPIs, start small and build up from there.
Each organization should select KPIs related to its risks and goals. Your objective is not to have eyes on everything but to put your time (and money) into mitigating the biggest risks.
These are some of the most effective cyber security KPI metrics that companies should pay close attention to. Let’s break them down into three types of metrics to provide some clarity.
Incident response metrics
Some of the most important cyber security KPI examples are incident response metrics that relate to detecting and mitigating incidents. Consider that cyberattacks have skyrocketed in the last two years, causing highly expensive and intrusive damage to companies of all types.
Incident response metrics answer the question, “Is my organization able to identify threats and then address them?”
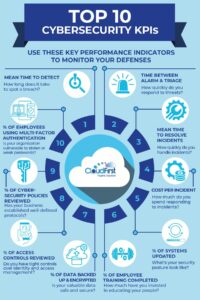
#1: Mean time to detect (MTTD)
MTTD measures how long it takes your cyber security team to detect an incident. Obviously, faster is better.
IBM’s report from 2020 found that it took 280 days for the average business to detect a data breach. Imagine the havoc that can happen in that time. An M-Trends report found that in 2018 threats remained on networks for as long as 204 days before being detected. It is a very real risk. The goal here is, of course, to detect threats in the shortest possible amount of time.
#2: Time between alarm and triage
The time between alarm and triage is a metric that focuses on how fast your team responded to the threat. How responsive were they? Was it fast enough?
Quality response metrics
Now that your team has detected a problem, how do they handle it? With quality response metrics, the goal is to determine if your current framework is able to provide support when needed. Here, the question you’re answering is, “Did my framework respond fast enough, and how much did it hurt?”
#3: Mean time to resolve (MTTR)
MTTR is a common metric to monitor, looking at the time it took for your team to become aware of the incident, make the decision to resolve it, and then handle it. It provides insight into exactly how long it took to resolve the problem, exposing your window of risk.
#4: Cost per incident
Cost per incident is one of the most important metrics from a business management standpoint. It helps you see the cost of responding to and resolving the breach. It includes all employee-related costs, activity suspension repercussions, loss of communication with customers, downtime for your system, and associated costs.
Consider a widescale event, one in which the attacker gains access to customer files or sensitive data. IBM notes that the average global cost of a data breach is $4.45M. That’s increased about 15% in the last three years. In 2023, 550 organizations experienced a data breach.
Preventive metrics
Preventive metrics are a bit more challenging to understand because, well, not a whole lot happens here if things are going well. These metrics help you track your progress over time to determine if your initiatives are benefiting your company. The question you are answering here is, “Is my cybersecurity framework succeeding over time and improving outcomes as a result?”
There’s no hard figure that’s ideal to reach in these areas. Rather, look at your progression over time. Is it improving? Is it lagging?
#5: Percentage of systems updated
How up-to-date are your systems? Where are the gaps in them? You should see this figure improving over time.
#6: Percentage of technical and nontechnical employee security training completed
Employee security training is core to improving cyber security risk. Many organizations should focus on how well-trained employees are and work to consistently improve this figure.
#7: Percentage of data backed up and encrypted
Data backup is an understandable task to overlook. Automated cloud backups make this mistake easier to avoid. Tracking data backup percentages and encryption helps you monitor the overall protection of that data.
#8: Percentage of access restrictions and admin rights reviewed/in need of review
Access restriction is foundational to protecting business information and sensitive data. Tracking who tries to access your data and how often administration access is given, along with how efficient the review process is, can help you keep your business on track.
#9: Percentage of cybersecurity policies reviewed/in need of review
Cybersecurity policies need to be reviewed and maintained over time. This is a task that’s often put off but needs to be monitored.
#10: Percentage of employees using multi-factor authentication
Employees may push back against multi-factor authentication (MFA) because it adds an extra step to their sign-in process. However, MFA is crucial for protecting against stolen or weak passwords.
These are some cyber security KPI examples, but this list doesn’t include all of them by any means. You don’t have to feel overwhelmed by trying to track every metric. Start with these and then customize your focus based on the risks to your company.
How KPIs can tell you if a cyber security program is effective
One of the most effective ways to boost organizational efficiencies is to reduce business and regulatory risk, including through the use of KPIs.
Why does this matter? What does looking at a few metrics do for you, the business owner who isn’t in the trenches trying to prevent data breaches and ransomware attacks?
Like every other part of your business, you have to monitor it as closely to real time as possible to know how well it’s working. You wouldn’t keep pumping money into an ad campaign that’s failing miserably or put time into a new product launch that lacks substance.
To measure the success of your cyber security program, you have to establish KPIs and then monitor them over time. Because these are trackable figures, they create a very clear indication of what’s actually happening. Just like your sales reports, they give you data you can use to make decisions.
If a cybersecurity KPI is worrisome to you, such as how much each incident costs your company, you can zero in on how to improve that specific area. KPIs are an actionable tool.
How to collect data, monitor progress, and understand KPIs

Now that we have a good understanding of the cyber security KPI metrics to monitor, how do we do it?
Assign the necessary team
This falls on the shoulders of the chief information security officer, but it’s also important for all senior leaders within your organization to understand. You should assign specific people to handle various roles and hold them accountable.
Establish scorecards and goals
Then you need to have a process in place to evaluate your KPIs. Otherwise, you’re wasting your time.
You should have scorecards that outline your goals and establish parameters for each KPI. On a consistent basis, your team should pull the necessary data to measure performance in each area. Whenever possible, automate data management. This minimizes stress on every member of the team.
Monitor data on a routine, consistent basis
This should happen on a regular schedule to establish clear, well-defined indications of improvement. You’ll need to assign the frequency of measurements based on where your risks lie, whether that’s daily, weekly, or monthly. Some metrics require more careful oversight than others.
Evaluate data on a formal basis
Leaders need to meet regularly with their cybersecurity team members. This isn’t something you just put in place and wait to hear about later. Instead, be proactive by scheduling formal debriefing sessions.
Cyber security KPI metrics like these answer important questions, but if you don’t use the information to formulate improvements, your company could be exposed to risk. The right tools, framework, and resources make creating and managing risk factors easier, less time-consuming, and more effective.
There’s much more to talk about when it comes to cyber security, including getting ISO 27001 certification and putting in place formal recovery strategies. Yet beyond this, we must focus on cybersecurity’s foundation: the metrics that define whether your current security methods are effective.
Don’t be overwhelmed by the lingo. It’s all about creating protection for your company, measuring if it’s working, and addressing problems if necessary.
We can help you. To get the information you need now, download our ebook.

