Don’t settle for a subpar security operations center. According to IBM’s annual Cost of a Data Breach Report 2024, the average cost of a data breach has surged to nearly $5M. The money you’ll spend investing in a solid security operations center team is nothing compared to the cost of not having one.
With this in mind, you may be wondering: What is a security operations center (SOC)?
Excellent question.
An SOC is a team of IT professionals—including security operations center analysts—who improve an organization’s threat detection and its response and prevention capabilities by unifying and coordinating all cybersecurity technologies and operations.
That’s a tall order, and it takes the right blend of cybersecurity professionals and technology to make it happen.
The necessity of an SOC is clear when you look at the cost of a breach. The right SOC team can help to prevent countless breaches, earning their spot in the squadron ten times over.
According to IBM, one in three breaches involves shadow data (any created, stored, or shared data that exists outside the centralized and secured data management framework). The proliferation of data stored across multiple locations is making it harder to track and safeguard.
The more experienced cybersecurity professionals there are on the lookout for suspicious behavior—and the better equipped they are with the proper tools—the less likely shadow data is to lead to a breach.
That said, it can be cumbersome to know what to look for, as well as what to avoid, to find an SOC that meets the automation requirements of an effective cybersecurity defense system today.
How AI-driven automation supports your security operations center

Cybersecurity automation is key to maximizing the efforts of your SOC team. We at CloudFirst understand this intimately in our dedication to business continuity and cyber resilience, and that’s why ezAutomate pairs perfectly with our IBM i Security service—SOC included. We ensure your sensitive data and mission-critical applications are Fort Knox–level secure 24-7, 365, so you can rest easy.
AI-driven automation is a crucial addition when building an effective SOC that can stand against current threats without cutting too deeply into the company budget. In fact, IBM reports that adopting security AI and automation can cut breach costs significantly, with an average of over $2M in savings.
As Forbes Councils Member Thangaraj Petchiappan says, “An SOC powered by AI supercharges threat detection and response efforts.“ He also explains how these SOCs have evolved to provide automated threat detection, enhanced accuracy, and fast response time.
When properly leveraged, cybersecurity automationi can, for example, take repetitive tasks that typically take around 30 minutes to complete and boil them down to as little as 40 seconds. Time savings is one of the most frequently referenced perks of security automation.
But AI-driven automation is not the only key player for an effective SOC. There are a few traits to watch for to get the most bang for your buck.
Top traits of an effective security operations center

SOCs provide the ideal opportunity for humans and machines to work together for the betterment of cybersecurity. Without optimizing operations through tech, defenses can fall short and personnel can quickly be consumed by tedious tasks.
The ideal blend of technology and human touch can be a delicate balance, but it’s one worth achieving in order to obtain consistent, successful results.
Each SOC typically has four main tiers:
- Triage Specialist (raw data collection and analysis)
- Incident Responder (in-depth assessment using threat intelligence)
- Threat Hunter (proactive threat detection and critical security alert review)
- SOC Manager (hiring, training, and evaluation of team members, process creation, incident report assessment, etc.)
The success of these team members partly depends on the resources they have access to. Any effective SOC must, at the very least, be able to ingest and organize data, detect security events, and predict potential threats.
But to face today’s bad actors, your SOC should also automate tasks, orchestrate across different integrations, and even recommend next steps in the face of a detected threat.
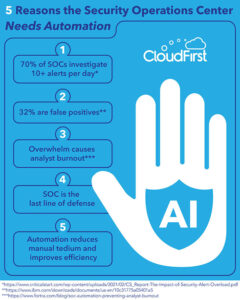
Splunk predicts that 90% of tier-1 analyst work will be automated in the coming years. That may be startling to some, but it only means more time for specialized work and dedicated time for other cybersecurity responsibilities. The increase in automating repetitive tasks can also help prevent analyst burnout.
In a 2019 report from Critical Start on The Impact of Security Alert Overload, they found that alert fatigue is still prevalent across SOCs, with more than 70% investigating 10 or more alerts per day.
The amount of data an SOC sifts through daily varies by industry and company size, but one thing remains consistent: SOC analysts are flooded with false positives, with SOCs reporting that 32% of incidents turn out not to be real threats.
One of AI’s specialties is pattern recognition across large sets of data, which can reduce time spent on false positives and give analysts time back in their day.
Cybersecurity automation remains one of the most straightforward ways to address these pain points. Keeping operations the way they are—with both time spent per alert and turnover rates steadily increasing—is not sustainable.
The SOCs that thrive are the ones that continuously evolve.
As Emil Sayegh, a serial technology CEO, says for Forbes, “A robust SOC should continually strive for operational improvements. Any sign of stagnation or a lack of active efforts to enhance processes should raise concerns.”
A day in the life of an SOC team can be head-spinning, and the right tech can put a damper on the flames—or stop them from catching to begin with.
Let’s walk through a few of the main players and how they apply AI to their SOCs to get an idea of what these ideas look like in practice.
How some of the best SOCs use AI (and the importance of an SLA)
Two important aspects to consider when deciding whether to work with an external SOC team or build your own are how they leverage AI and what their service level agreements (SLAs) look like.
As IBM says, “SLAs set customer expectations, hold providers accountable, and ultimately help optimize the end-user experience. SLAs pave the way for a smoother working relationship, settling uncertainty and points of contention from the start, and help protect the interests of all parties involved.”
You should know what you’re getting into before signing on with any SOC provider. These factors are also a great frame of reference for how to apply AI to your own SOC and structure your SLA if needed.
For example, Crowdstrike leans into AI-driven automation for:
- enhanced threat detection
- incident handling
- threat intelligence
Doing so frees up cyber professionals to focus on the more complex aspects of cybersecurity. In their service level agreement, Crowdstrike outlines Falcon Spotlight and how they provide holistic visibility, machine learning–based prioritization, and vulnerability-based analytics for risk assessment.
Crowdstrike’s SLA outlines the challenges present in the industry, their partnerships, how their solution addresses those challenges, the business value of their service, and the key capabilities of their software.
Cybersecurity automation doesn’t happen by accident. The long hours spent refining and improving these services are testaments to that fact.
Arctic Wolf Networks, Inc. is another prime example of SOC as a service, offering 24-7 monitoring, threat detection, and incident response capabilities, leveraging a combination of AI-driven analytics and human expertise.
As Arctic Wolf reports, “Most organizations lack complete visibility into their security infrastructure and face more than 10,000 alerts per day, which leads to alert fatigue and blind spots in coverage.” This, paired with a lack of threat intelligence, leads to higher risk.
Applying AI to lighten the load is a no-brainer against those high alert numbers.
In Arctic Wolf’s SOC service, they manage:
- detection and response
- risk
- security awareness
- incident response
IBM i Security is another example of an SOC done right, with customizable packages that account for nuances across different organization sizes and needs.
These services include:
- realtime alerts for critical events defined by standard best practices
- customized security reports
- incident response and reports for management
- 100% uptime guarantee
Each of these providers recognizes the importance of keeping pace with cyber threats through AI-driven automation that supports a strong SOC and, ultimately, prevents expensive breaches that threaten mission-critical applications and sensitive data.
Is your hybrid environment protected?
Did you know that, according to IBM, 40% of data breaches involved data stored across multiple environments? Breached data stored in public clouds incurred the highest average breach cost at $5.17M.
With hybrid environments becoming the new norm, securing data isn’t getting any easier—unless you start applying AI-driven automation to your SOC.
So, is your hybrid environment protected?
SOC teams are only as good as their technology. Help them achieve all they can by equipping them with the tools they need to exceed expectations.
CloudFirst can help you get there. Don’t wait until it’s too late to reach out.

